 Introduction to Cybersecurity Risk Mitigation
Introduction to Cybersecurity Risk Mitigation
In today’s interconnected world, businesses, government agencies, and individuals are more vulnerable than ever to a variety of cybersecurity threats. Cybersecurity risk mitigation is a proactive approach to protecting systems, networks, and data from these risks. In this part of the article, we will define cybersecurity risk mitigation, highlight the importance of addressing cybersecurity risks, and explore the different types of risks organizations face. We will also discuss the fundamental principles of risk mitigation and introduce the common strategies employed to reduce cybersecurity risks.
What is Cybersecurity Risk Mitigation?
Cybersecurity risk mitigation refers to the process of identifying, assessing, and reducing the risks that can negatively impact an organization’s information systems and data security. The primary goal is to minimize the likelihood and impact of cybersecurity threats, such as hacking, phishing, malware, and insider threats. Effective cybersecurity risk mitigation helps prevent financial losses, reputational damage, and legal consequences resulting from data breaches and other cyberattacks.
The process involves a combination of preventive measures, monitoring, and ongoing risk management practices to safeguard an organization’s assets. It is crucial in today’s business landscape, where cyberattacks can severely disrupt operations and compromise sensitive information.
Why is Cybersecurity Risk Mitigation Important?
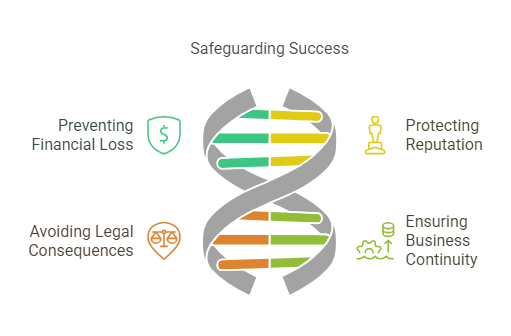
With the increasing sophistication of cyber threats, organizations of all sizes are at risk of cyberattacks. Cybersecurity risk mitigation is essential for several reasons:
- Preventing Financial Loss: Data breaches and cyberattacks can result in significant financial losses. Costs can include fines, legal fees, loss of business, and expenses related to recovering from the attack.
- Protecting Reputation: A compromised security system can severely damage a company’s reputation. Customers and clients expect businesses to protect their personal information, and failure to do so can erode trust.
- Avoiding Legal Consequences: Organizations must comply with regulations that mandate the protection of sensitive data (such as GDPR, HIPAA, and CCPA). Failure to comply can result in legal penalties and lawsuits.
- Ensuring Business Continuity: Cyberattacks can disrupt operations, leading to downtime, loss of productivity, and the potential compromise of critical systems. Risk mitigation helps ensure business continuity by protecting against these disruptions.
Types of Cybersecurity Risks Organizations Face
Organizations face various types of cybersecurity risks, each with its own potential impact. Here are some of the most common cybersecurity risks:
- Data Breaches: Data breaches occur when unauthorized individuals gain access to sensitive or confidential information. These breaches can lead to identity theft, financial fraud, and loss of customer trust.
- Phishing Attacks: Phishing attacks involve deceptive emails or websites designed to trick individuals into revealing personal or financial information. Cybercriminals often impersonate legitimate organizations to gain access to sensitive data.
- Ransomware Attacks: Ransomware is a type of malicious software that encrypts an organization’s data, rendering it inaccessible. Cybercriminals demand payment (usually in cryptocurrency) in exchange for the decryption key.
- Insider Threats: Insider threats come from employees, contractors, or other individuals within the organization who misuse their access to steal data or cause harm. These threats can be intentional or accidental.
- Denial-of-Service (DoS) Attacks: A DoS attack overwhelms a system or network with traffic, causing it to become unavailable to users. Distributed Denial-of-Service (DDoS) attacks, which use multiple sources to launch an attack, are particularly damaging.
- Advanced Persistent Threats (APTs): APTs are prolonged, targeted attacks by cybercriminals or nation-state actors. These attackers infiltrate networks to steal sensitive information over an extended period without being detected.
The Basic Principles of Cybersecurity Risk Mitigation
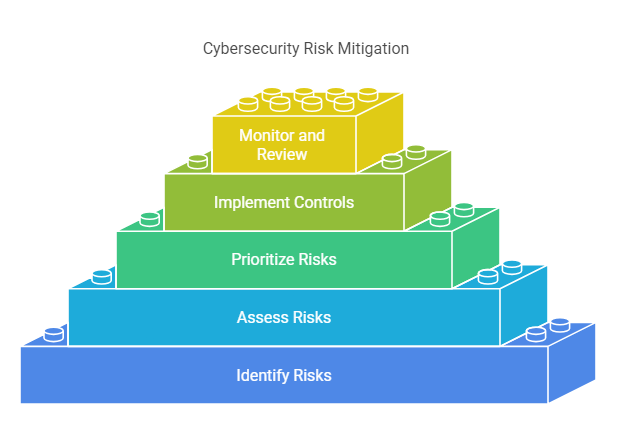
The core principles of cybersecurity risk mitigation are:
- Identify Risks: The first step in risk mitigation is to identify the potential cybersecurity risks. This involves understanding the organization’s critical assets, infrastructure, and vulnerabilities.
- Assess Risks: Once risks are identified, they must be assessed for their likelihood and potential impact. This helps organizations prioritize which risks to address first.
- Prioritize Risks: Not all risks are equal. Some risks may have a more significant impact on the business than others, so it is essential to prioritize them based on their potential damage to the organization.
- Implement Controls: Mitigation controls, such as firewalls, encryption, and employee training, should be implemented to reduce identified risks. These controls should be tailored to address specific risks based on their likelihood and impact.
- Monitor and Review: Cybersecurity is an ongoing process. Continuous monitoring of systems, networks, and employee behavior is critical for detecting and responding to emerging threats.
Common Strategies Used in Cybersecurity Risk Mitigation
Several strategies are employed in cybersecurity risk mitigation. These strategies help businesses reduce the likelihood of a successful cyberattack or minimize its impact if it occurs. Below are the most commonly used strategies:
| Cybersecurity Risk Mitigation Strategy | Description |
|---|---|
| Risk Avoidance | Taking steps to avoid activities or situations that could expose the organization to risk (e.g., not using outdated software). |
| Risk Reduction | Implementing measures to reduce the likelihood or impact of a risk (e.g., using encryption, updating software regularly). |
| Risk Transfer | Transferring the risk to a third party, such as purchasing cybersecurity insurance or outsourcing certain security tasks. |
| Risk Acceptance | Accepting the risk when it is not feasible or cost-effective to mitigate it (e.g., for minor risks with minimal impact). |
Strategies and Best Practices for Cybersecurity Risk Mitigation
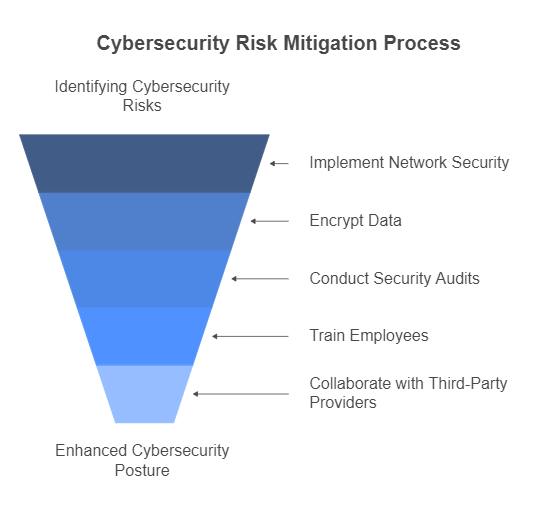
Cybersecurity risk mitigation is not a one-time task but a continuous process that requires organizations to implement effective strategies, assess evolving threats, and adopt best practices to protect their systems and data. In this section, we’ll explore various strategies and best practices that organizations can adopt to effectively mitigate cybersecurity risks.
Effective Strategies for Cybersecurity Risk Mitigation
Organizations can implement various strategies to protect against the ever-evolving landscape of cyber threats. These strategies are based on the identified risks and the impact they could have on business operations. Here are some of the most effective strategies:
- Network Security Measures
Network security is the foundation of any cybersecurity risk mitigation strategy. Protecting the network from malicious intrusions or unauthorized access is critical for safeguarding organizational data and ensuring business continuity. Several components are involved in network security, including:
- Firewalls: Firewalls are hardware or software-based systems that filter traffic between an internal network and external networks (such as the internet). They help prevent unauthorized access to sensitive information by blocking or allowing certain types of network traffic based on predefined security rules.
- Intrusion Detection Systems (IDS): IDS are designed to detect and alert on suspicious activities or potential threats within a network. These systems monitor network traffic for abnormal patterns or signs of cyberattacks, such as unusual login attempts or data exfiltration.
- Intrusion Prevention Systems (IPS): IPS go one step further than IDS by actively blocking malicious traffic or attacks. These systems can take immediate action to prevent a detected intrusion, such as terminating a malicious session or blocking a suspicious IP address.
- Virtual Private Networks (VPNs): VPNs encrypt internet traffic to secure data transmission across public networks. Employees working remotely or accessing company systems from unsecured locations can use VPNs to ensure their connections are safe from cybercriminals.
- Data Encryption and Protection
Encryption is one of the most effective ways to safeguard sensitive information in transit and at rest. Encryption converts readable data into unreadable ciphertext, which can only be deciphered with an encryption key. By implementing strong encryption protocols, organizations can ensure that even if data is intercepted, it will be unreadable to unauthorized individuals.
Additionally, encryption should be used in combination with other data protection measures, such as:
- Backup Solutions: Regularly backing up data is an essential step in reducing the risk of data loss or damage due to cyberattacks. In the event of a ransomware attack or data breach, having encrypted backups allows organizations to restore their systems without paying the ransom or suffering from long-term damage.
- Access Control: Limiting access to sensitive data is another important aspect of data protection. Implementing access control policies that restrict access based on roles or job responsibilities helps prevent data breaches caused by insider threats or unauthorized access.
- Data Masking: For particularly sensitive data, organizations can use data masking techniques, where sensitive information is replaced with fictitious data. This is often used in environments like testing or development to protect customer data from accidental exposure.
- Regular Security Audits and Penetration Testing
Conducting regular security audits and penetration testing are essential practices in identifying weaknesses in an organization’s security posture. These activities help identify potential vulnerabilities that could be exploited by cybercriminals.
- Security Audits: A security audit involves a thorough examination of an organization’s security policies, procedures, and practices. Auditors assess how well the organization’s security systems are implemented, whether they comply with internal policies and industry standards, and whether there are any gaps in the security infrastructure. Regular audits help organizations remain compliant with regulations, such as HIPAA, PCI-DSS, or GDPR, and identify areas of improvement in their security practices.
- Penetration Testing: Penetration testing, also known as ethical hacking, involves simulating a cyberattack on the organization’s systems to identify vulnerabilities before cybercriminals can exploit them. Ethical hackers attempt to exploit vulnerabilities and provide recommendations to mitigate these risks. Penetration testing can be conducted periodically or after major system updates to ensure that newly introduced changes don’t create security gaps.
- Employee Training on Cybersecurity Best Practices
Employees are often the weakest link in an organization’s cybersecurity defenses. Phishing attacks, social engineering tactics, and poor password management can provide cybercriminals with easy access to systems and data. Thus, employee training is crucial in creating a culture of security within the organization.
- Phishing Awareness: One of the most common tactics used by cybercriminals is phishing, where they trick employees into revealing sensitive information like login credentials or financial details. Training employees to recognize phishing emails and other types of social engineering tactics can significantly reduce the risk of falling victim to these attacks.
- Password Management: Weak or reused passwords are another common entry point for attackers. Employees should be trained to use strong, unique passwords for each account and system. Password management tools can also be provided to help employees securely store and manage their passwords.
- Incident Reporting: Employees should be encouraged to report suspicious activities or potential security incidents to the appropriate team or department immediately. Prompt reporting can help organizations contain threats early, reducing their potential impact.
- Utilizing Cybersecurity Frameworks
Cybersecurity frameworks provide organizations with a structured approach to managing and mitigating cybersecurity risks. These frameworks help businesses identify their security needs, implement best practices, and measure their progress toward improving security posture. Some popular frameworks include:
- National Institute of Standards and Technology (NIST) Cybersecurity Framework: NIST provides a set of standards and guidelines designed to help organizations manage cybersecurity risks. The NIST Cybersecurity Framework is widely adopted in both the private and public sectors and is recognized for its effectiveness in reducing cyber risks.
- Center for Internet Security (CIS) Controls: The CIS Controls are a set of prioritized cybersecurity best practices that help organizations secure their networks. These controls focus on specific actions, such as inventorying software, securing configurations, and detecting and responding to attacks.
- ISO 27001: The ISO 27001 standard is part of the ISO 27000 family of standards, which focuses on information security management systems (ISMS). ISO 27001 helps organizations ensure that they have effective measures in place to protect their data and meet compliance requirements.
- Collaborating with Third-Party Security Providers
Many organizations rely on third-party security providers to help mitigate cybersecurity risks. These providers offer a range of services, including threat intelligence, incident response, and managed security services. Partnering with experienced security vendors can provide the following benefits:
- Threat Intelligence: Third-party security vendors can provide real-time threat intelligence, helping organizations stay informed about the latest cyber threats. This allows businesses to adjust their cybersecurity strategies accordingly and respond faster to emerging risks.
- Managed Security Services (MSS): Managed Security Service Providers (MSSPs) can help organizations monitor their networks 24/7 for potential threats. MSSPs can manage firewalls, intrusion detection systems, and other security tools, allowing organizations to focus on core business functions while ensuring their systems remain protected.
- Incident Response: In the event of a cybersecurity breach, third-party security providers can assist with incident response. These providers have the expertise to contain the breach, assess the damage, and recover data, minimizing the impact on the business.
- Cost-Benefit Analysis of Cybersecurity Risk Mitigation
While implementing cybersecurity risk mitigation strategies can involve significant upfront investment, the cost of not doing so can be far greater. Cyberattacks can result in financial losses, legal liabilities, and reputational damage that could take years to recover from. A proactive cybersecurity strategy is often much less expensive than responding to a breach after it occurs.
Performing a cost-benefit analysis can help organizations understand the potential ROI of investing in cybersecurity risk mitigation. The cost of tools, software, training, and professional services must be weighed against the potential financial losses from cyberattacks, lawsuits, and compliance penalties.
In the ever-evolving landscape of cybersecurity, businesses need reliable partners to help mitigate risks effectively. Rapid Hire Solutions plays a crucial role in assisting organizations by providing tailored cybersecurity risk mitigation services. From conducting comprehensive security audits to helping implement robust cybersecurity frameworks, Rapid Hire Solutions ensures that businesses are well-equipped to handle potential threats. By leveraging their expertise, organizations can build resilient cybersecurity strategies, reduce vulnerabilities, and maintain compliance with industry regulations.
Legal Aspects, FAQs, and Conclusion
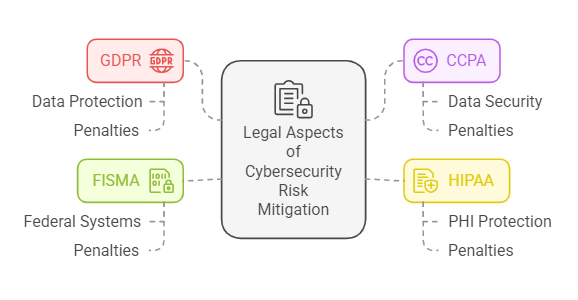
Cybersecurity risk mitigation is not only a business and operational concern but also has significant legal implications. Understanding the legal aspects, compliance requirements, and the consequences of failing to implement strong cybersecurity measures is crucial for organizations. This section will explore the legal aspects of cybersecurity, answer frequently asked questions, and conclude with key takeaways for implementing effective risk mitigation strategies.
Legal Aspects of Cybersecurity Risk Mitigation
In today’s increasingly digital world, organizations must adhere to various legal and regulatory requirements that govern the protection of sensitive data and the management of cybersecurity risks. Compliance with these regulations is not only necessary to avoid legal penalties but also essential for building trust with customers, partners, and regulators. Let’s explore some of the key legal frameworks and their impact on cybersecurity risk mitigation:
- General Data Protection Regulation (GDPR)
The GDPR is a regulation enacted by the European Union to protect the privacy and personal data of EU citizens. Although it applies primarily to organizations operating within the EU, any company worldwide that processes or stores data about EU citizens must comply with the GDPR.
- Relevance to Cybersecurity: GDPR mandates strict data protection and cybersecurity measures to ensure that personal data is safeguarded against unauthorized access, loss, or theft. Organizations are required to implement appropriate technical and organizational measures to protect data, and they must notify authorities of any data breach within 72 hours.
- Penalties: Non-compliance with the GDPR can result in significant penalties, with fines reaching up to 4% of global annual turnover or €20 million (whichever is higher).
- California Consumer Privacy Act (CCPA)
The CCPA is a state-level regulation that grants California residents greater control over their personal data and imposes obligations on businesses to safeguard it. Similar to the GDPR, it mandates organizations to implement strong cybersecurity measures and practices to protect personal information.
- Relevance to Cybersecurity: The CCPA emphasizes data security by requiring businesses to implement “reasonable” security procedures and practices to prevent data breaches. It also provides consumers with the right to know what data is being collected about them, request its deletion, and opt out of its sale.
- Penalties: Businesses that violate the CCPA can face fines of up to $2,500 per violation or $7,500 for each intentional violation.
- Health Insurance Portability and Accountability Act (HIPAA)
The HIPAA Privacy and Security Rules govern the handling of personal health information (PHI) by covered entities such as healthcare providers, insurers, and business associates. The regulation mandates the protection of PHI through robust cybersecurity measures.
- Relevance to Cybersecurity: HIPAA requires healthcare organizations to implement encryption, secure access controls, and regular risk assessments to protect PHI from cyber threats. The regulation also mandates breach notification procedures and ensures individuals’ right to access their health data.
- Penalties: Non-compliance with HIPAA can result in severe penalties, including civil fines ranging from $100 to $50,000 per violation and criminal penalties for intentional violations.
- The Federal Information Security Modernization Act (FISMA)
FISMA is a U.S. federal law that mandates the protection of federal information systems by government agencies and contractors. This law sets standards for cybersecurity and data protection within federal agencies.
- Relevance to Cybersecurity: FISMA requires federal agencies and contractors to implement risk-based security programs, conduct regular assessments, and report incidents. It also defines specific cybersecurity standards and guidelines that must be adhered to.
- Penalties: Organizations that fail to comply with FISMA regulations may face penalties, loss of contracts, and reputational damage.
- The Role of Compliance in Mitigating Legal Risks
Adherence to regulatory frameworks such as GDPR, CCPA, HIPAA, and others is essential for mitigating legal risks. Non-compliance with these regulations can lead to heavy fines, legal battles, and reputational damage. In addition, organizations may also face lawsuits from affected individuals or customers if their data is compromised.
By ensuring compliance, businesses not only avoid legal consequences but also enhance their credibility and reputation. Organizations should regularly audit their cybersecurity practices to ensure they meet current legal and regulatory standards.
FAQs: Answering Common Questions About Cybersecurity Risk Mitigation
Here are five frequently asked questions about cybersecurity risk mitigation that can help clarify common concerns and guide businesses in protecting their digital assets:
What is cybersecurity risk mitigation, and why is it important for businesses?
Cybersecurity risk mitigation refers to the process of identifying, assessing, and reducing potential threats to an organization’s information systems. It involves implementing strategies, tools, and best practices to prevent cyberattacks, data breaches, and other security incidents. It is crucial for businesses because cyber threats can lead to significant financial losses, data breaches, reputational damage, and legal consequences. Mitigating cybersecurity risks ensures business continuity and protects sensitive data from malicious actors.
How can a company assess its cybersecurity risks?
A company can assess its cybersecurity risks through risk assessments and audits. This process involves identifying potential vulnerabilities, evaluating the likelihood and impact of various threats, and prioritizing them based on their potential consequences. Tools such as vulnerability scanners, penetration testing, and threat intelligence reports can assist organizations in assessing their security posture and identifying areas for improvement.
What are the best practices for mitigating cybersecurity risks in a small business?
For small businesses, the following best practices can significantly reduce cybersecurity risks:
- Implement strong password policies and multi-factor authentication (MFA).
- Regularly back up data and use encryption to protect sensitive information.
- Train employees on phishing awareness and secure online practices.
- Use firewalls and antivirus software to monitor and block malicious activities.
- Regularly update software and systems to patch vulnerabilities.
How does encryption help in cybersecurity risk mitigation?
Encryption helps mitigate cybersecurity risks by converting data into an unreadable format, making it inaccessible to unauthorized users. Even if cybercriminals intercept encrypted data, they cannot read or exploit it without the decryption key. Encryption is particularly important for protecting sensitive information like financial records, personal data, and intellectual property, both during transmission and while stored.
What cybersecurity frameworks can help organizations structure their risk mitigation plans?
Several cybersecurity frameworks can help organizations structure their risk mitigation efforts:
- NIST Cybersecurity Framework: A flexible framework that provides a comprehensive approach to identifying, protecting, detecting, responding to, and recovering from cyber incidents.
- ISO 27001: A globally recognized standard for establishing an Information Security Management System (ISMS).
- CIS Controls: A set of 20 critical security controls that provide actionable steps for securing organizational assets.
Conclusion
Cybersecurity risk mitigation is an ongoing process that involves identifying, assessing, and mitigating potential threats to an organization’s data and systems. By implementing robust cybersecurity strategies, such as network security, data encryption, regular audits, and employee training, organizations can significantly reduce the risk of cyberattacks and data breaches.
Legal and regulatory compliance, including adherence to frameworks like GDPR, HIPAA, and FISMA, is essential for mitigating legal risks and ensuring that organizations maintain trust with customers, employees, and partners.
Businesses that invest in cybersecurity risk mitigation benefit from reduced financial and reputational risks, compliance with laws, and improved operational efficiency. To effectively implement a cybersecurity risk mitigation strategy, businesses can seek professional assistance from security experts and service providers to ensure that their cybersecurity practices remain current, comprehensive, and compliant.
